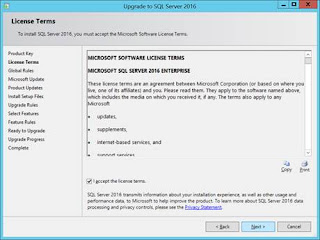
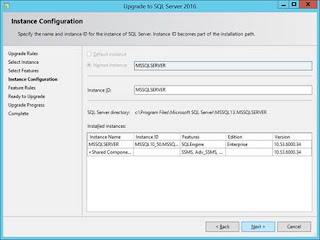
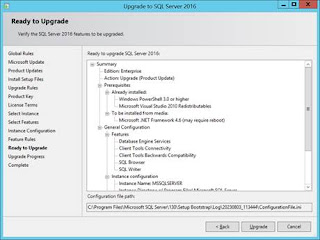
Definition of done
Discussing the "Definition of Done" (DoD) during the Sprint Retrospective is essential for the continuous improvement of the Scrum team. The DoD serves as a crucial agreement on the criteria that must be met for a user story or task to be considered complete. By revisiting and discussing the DoD in the retrospective, the team has an opportunity to reflect on whether the agreed-upon standards were consistently met during the sprint. This discussion allows the team to identify any deviations, challenges, or areas of improvement related to the DoD. Addressing these issues ensures that the team maintains a shared understanding of quality expectations and collectively works towards refining and adhering to the DoD in future sprints. Regularly revisiting and refining the Definition of Done contributes to the overall effectiveness of the development process, leading to higher-quality deliverables and increased customer satisfaction.
Team relations
Examining team relations during the Sprint Retrospective holds paramount importance in nurturing a healthy and collaborative working environment. Openly discussing team relations allows team members to address any interpersonal challenges, fostering improved communication and mutual understanding. By exploring dynamics within the team, the retrospective provides an opportunity to identify and resolve conflicts, enhance collaboration, and reinforce a positive team culture. Addressing team relations during the retrospective promotes a sense of transparency and trust, empowering team members to express concerns, share perspectives, and collectively work towards building strong, cohesive relationships. This emphasis on interpersonal dynamics contributes not only to the team's well-being but also to its overall productivity and success in future sprints.
In conclusion, the discussions around the "Definition of Done" (DoD) and
"Team Relations" during the Sprint Retrospective are pivotal elements
for the continuous improvement and success of a Scrum team. Revisiting
and refining the DoD ensures a shared understanding of quality
standards, promoting the consistent delivery of high-quality increments.
Simultaneously, addressing team relations fosters a collaborative and
positive working environment. Open communication about interpersonal
dynamics helps identify and resolve conflicts, strengthening team bonds
and contributing to a healthier team culture. Together, these
discussions empower the team to enhance both the technical and
interpersonal aspects of their work, paving the way for sustained
improvements and a more effective Scrum framework in future sprints.